How to Run Security Threats Diagnostics
Read below how you can prevent the most commonly known vulnerabilities within the OWASP Top 10 APIs attack vector.


Corporate wide operations are broadly supported by IT systems' integrations and rely strongly on data exchange and transfer across departments and stakeholders. While data exchange process is running between corporate wide functions, external partners (B2B) and consumer services (B2C), there is always a risk that sensitive data may get jeopardized. Luckily there are mechanisms that will help you to put in place counter measures to prevent the most commonly known vulnerabilities within the OWASP Top 10 attack vector.
What is OWASP Top 10 Security Risks?
OWASP (Open Web Application Security Project) is a nonprofit foundation that works to improve the security of software. In 2019 it has developed the Top 10 API Security Project that concentrates on strategies and solutions to understand and diminish the security threats and vulnerabilities that are inherent in today's APIs (Application Programming Interfaces).
Top 10 most critical vulnerabilities listed and explained:
Broken Object Level Authorization
Broken User Authentication
Excessive Data Exposure
Lack of Resources & Rate Limiting
Broken Function Level Authorization
Mass Assignment
Security Misconfiguration
Injection
Improper Assets Management
Insufficient Logging & Monitoring
How does breach during data exchange happen?
Data exchange happens regularly in daily operations of an organisation. It can happen via using excel sheets, pdfs, word documents, key notes, flat files and other textual files in addition to standard ETL processes (Extract-Transform-Load), as well as modern services, like REST / JSON, Web Services, SaaS, ERP, CRM, HR tools, and more. Most of the time, 40% of the data manipulation attempts and hacking happen behind a corporate firewall. This means that data is exposed for hacking by in-house employees or consultants. These technical data manipulation attempts can be done by several different kind of stakeholder roles such as IT database administrators, developers, testers and other personnel.
When the data flows across several business services, the hacked data, meanwhile, may contaminate various IT systems such as middleware database and operating system among other software services.
Risks on the rise
The trend shows that Digitalization and Modernization of legacy systems are moving towards open data-driven businesses and Internet-Of-Things (Iot). Business critical data gets exposed and published from mobile devices or B2B and B2C channels due to modernization and digitalization services of corporate open data strategy and interoperability demands from markets. When publishing data into the public internet (De-Militarized Zone), it might cause the underlying master data system to be challenged for data manipulation attempts due to open data accessibility.
There are many reasons for why security deagnistics is critical for a growing amount of open data services:
Data flow across databases, documents (excel, pdf, flat file and more) are exposed for data manipulation of hacking of the content
Sensitive data such as personal information and customer registers contains information which should not be exposed to public API (unknowingly deploying potentially sensitive APIs)
Both, a northbound traffic (Internet, B2B, B2C), and an internal southbound interface traffic (local area business service and daily operations) expose threats for business-critical data.
Prevention Mechanisms Explained
When building your business integrations with APIs, or managing SaaS, or mobile / web application, you need to take preventative measures to mitigate all potential risks. The risks and vulnerabilities can affect your systems from all fronts: you customer-facing and stakeholder-facing apps, as well as operations wide internal apps.
One way is to adopt an iPaaS platform in an organisation. iPaaS stands from Integration-Platform-as-a-Service. iPaaS solutions help you to ensure the security of you most critical systems and bring high-level API visibility through monitoring. The aim of the monitoring is to provide a top-down monitoring approach across multiple datasets and integration solutions or API's: You will get a comprehensive view of all your APIs, where they are used and how they are performing.
Some iPaaS may provide built-in mechanisms to prevent the most commonly known vulnerabilities within the OWASP-10 attack vector. Here you can see how you can set up those mechanisms with frends low-code iPaaS that does have such built-in mechanisms.
Vulnerabilities:
(Official definitions provided according to the OWASP)
1. Broken Object Level Authorization
Vulnerability exposed: APIs tend to expose endpoints that handle object identifiers, creating a wide attack surface Level Access Control issue. Object level authorization checks should be considered in every function that accesses a data source using an input from the user.
Prevention: frends iPaaS provides role-based authorization with both OAauth 2.0 based services and API keys based services.


With OpenID Connect and oAuth 2.0 you will need to connect your existing identity management system to frends, as frends does not offer an identity server by itself. This is done so also to prevent users and user management from splitting between multiple tools within the IT of the customer.
OpenID Connect and oAuth are most suitable to secure API's which server front end applications or systems directly. This means that the API consumer usually authenticates as the end-user directly rather than using "system" credentials.
2. Broken User Authentication
Vulnerability exposed: Authentication mechanisms are often implemented incorrectly, allowing attackers to compromise authentication tokens or to exploit implementation flaws to assume other user’s identities temporarily or permanently. Compromising a system’s ability to identify the client/user, compromises API security overall.
Prevention: frends provides role-based rule set for accessing Open API / Swagger based services.
3. Excessive Data Exposure
Vulnerability exposed: Looking forward to generic implementations, developers tend to expose all object properties without considering their individual sensitivity, relying on clients to perform the data filtering before displaying it to the user.
Prevention: frends provides an Open API based semantically coherent interfaces for both successful operations and declined operations. Platform provides mechanism to filter or white list IP-address blocks and deny or blacklist specific IP-address blocks.
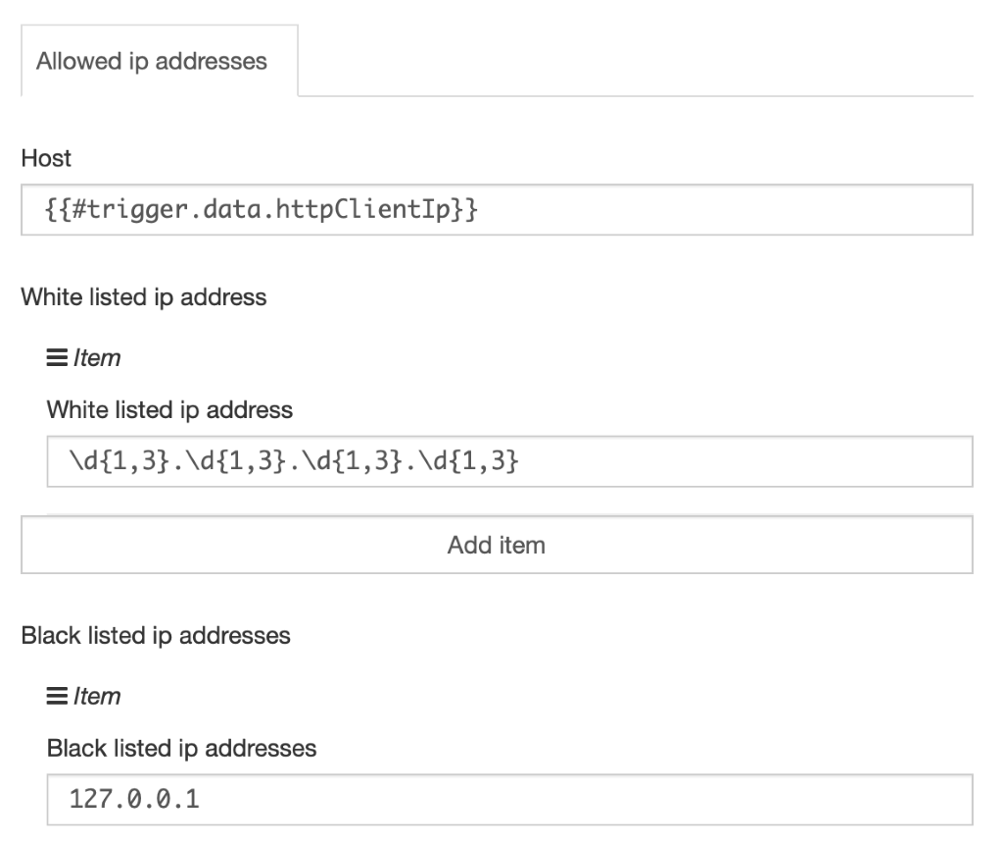

4. Lack of Resources & Rate Limiting
Vulnerability exposed: Quite often, APIs do not impose any restrictions on the size or number of resources that can be requested by the client/user. Not only can this impact the API server performance, leading to Denial of Service (DoS), but also leaves the door open to authentication flaws such as brute force.
Prevention: frends provides an Open API based semantically coherent interfaces for both successful operations and declined operations. For denial of services-based attacks frends provides threshold levels for transaction amounts per second.


5. Broken Function Level Authorization
Vulnerability exposed: Complex access control policies with different hierarchies, groups, and roles, and an unclear separation between administrative and regular functions, tend to lead to authorization flaws. By exploiting these issues, attackers gain access to other users’ resources and/or administrative functions.
Prevention: frends provides role-based rule set for accessing Open API / Swagger based services. These services can be secure with API key and define CRUD operations to support authorization on CRUD level.


6. Mass Assignment
Vulnerability exposed: Binding client provided data (e.g., JSON) to data models, without proper properties filtering based on an allowlist, usually leads to Mass Assignment. Either guessing objects properties, exploring other API endpoints, reading the documentation, or providing additional object properties in request payloads, allows attackers to modify object properties they are not supposed to.
Prevention: frends provides deep diagnostics to intercept and work as Web Application Firewall faulty Headers (only known headers are bypassed) on a TCP/IP HTTP protocol level and provides over 79 validation rules against commonly known attack vectors for payload attributes and working as intrusion detection back-end. Creating synchronizer token and hash keys with predefined salt to calculate attributes on requests is possible. Double encoding verifications for URL manipulation attempts can be applied.


7. Security Misconfiguration
Vulnerabililty exposed: Security misconfiguration is commonly a result of unsecure default configurations, incomplete or ad-hoc configurations, open cloud storage, misconfigured HTTP headers, unnecessary HTTP methods, permissive Cross-Origin resource sharing (CORS), and verbose error messages containing sensitive information.
Prevention: frends provides centralized configuration management for all the main and sub -processes for different environments and agent groups for dev, test, and production farms. Secured assets like passwords can be persisted into configuration management tool and information can be secured.


8. Injection
Vulnerabililty exposed: Injection flaws, such as SQL, NoSQL, Command Injection, etc., occur when untrusted data is sent to an interpreter as part of a command or query. The attacker’s malicious data can trick the interpreter into executing unintended commands or accessing data without proper authorization.
Prevention: frends provides deep diagnostics to intercept faulty messages and provides over 79 validation rules against commonly known attack vectors. These rules can be challenged against any data flowing from northbound and southbound interfaces.

9. Improper Assets Management
Vulnerability exposed: APIs tend to expose more endpoints than traditional web applications, making proper and updated documentation highly important. Proper hosts and deployed API versions inventory also play an important role to mitigate issues such as deprecated API versions and exposed debug endpoints.
Prevention: frends Control Panel provides user interface for staging environments such dev, test and production. Each environment has specific capabilities for publishing services and links using port openings. It is important to make routes through corporate secure routes inside trusted backbone services. Platform can be configured to publish through API gateway parameterisation related to the DNS name and link PORT.


10. Insufficient Logging & Monitoring
Vulnerability exposed: Insufficient logging and monitoring, coupled with missing or ineffective integration with incident response, allows attackers to further attack systems, maintain persistence, pivot to more systems to tamper with, extract, or destroy data. Most breach studies demonstrate the time to detect a breach is over 200 days, typically detected by external parties rather than internal processes or monitoring.
Prevention: frends provides a centralized monitoring window which provides filtering and zooming options for transactions. All of the events will be logged into the system and provides audit trail for bussiness critical operations.

